
Carding activity is when criminals try many stolen credit cards to place an order in a short period of time.
The final goal is to determine which cards are active and ready for purchases.
Magento 2 as any other eCommerce platform is at risk of a carding attack.
Payment gateways could punish stores that don't prevent online fraud.
It’s important to spot any unwanted activity and stop it as soon as possible.
I’ll list 7 anti-carding techniques that help to keep a Magento 2 website protected.
Disclaimer: All the solutions have one common drawback: it’s an extra point of failure. Your checkout will depend on a single service and its correct functionality.
Always track the conversion rate to make sure you don’t lose sales.
1. Google reCaptcha on the Checkout Page
If you are running Magento 2.4+ you could place Google reCaptcha on the checkout page.
Go to System > Configuration > Security > Google reCAPTCHA Storefront > Storefront > Enable for Checkout/Place Order:
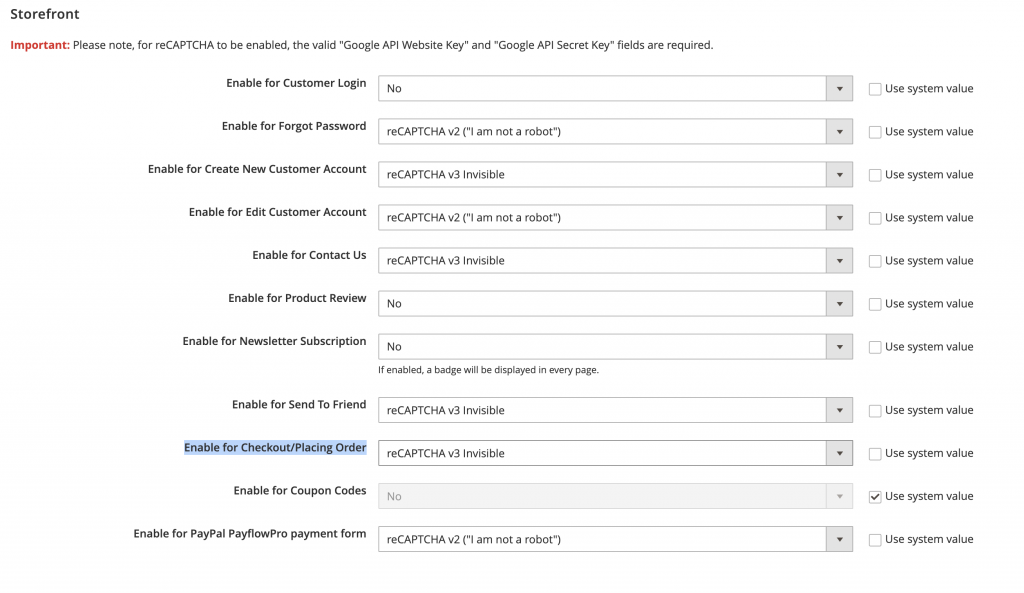
I’d recommend setting it to reCAPTCHA v3 Invisible. That way a potential customer doesn’t have to do or click anything extra to pass validation and place an order.
You will have to sign up for v3 reCAPTCHA on the google website and get API Website Key and API Secret Key. You will enter them on the same page:
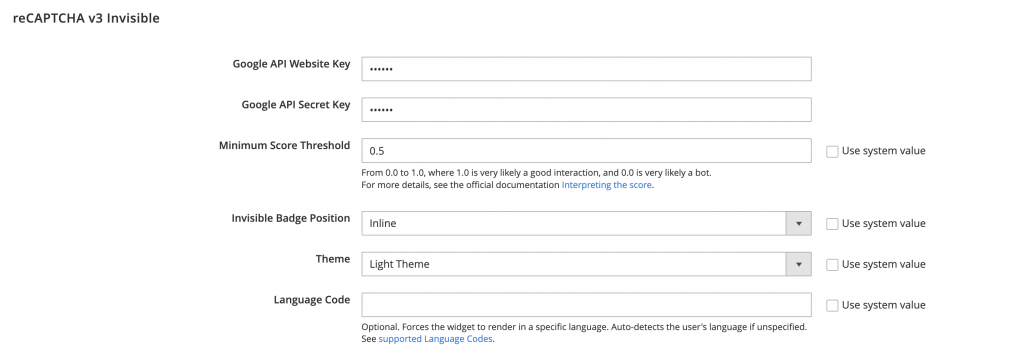
Once you set it up the payment page will look like this:
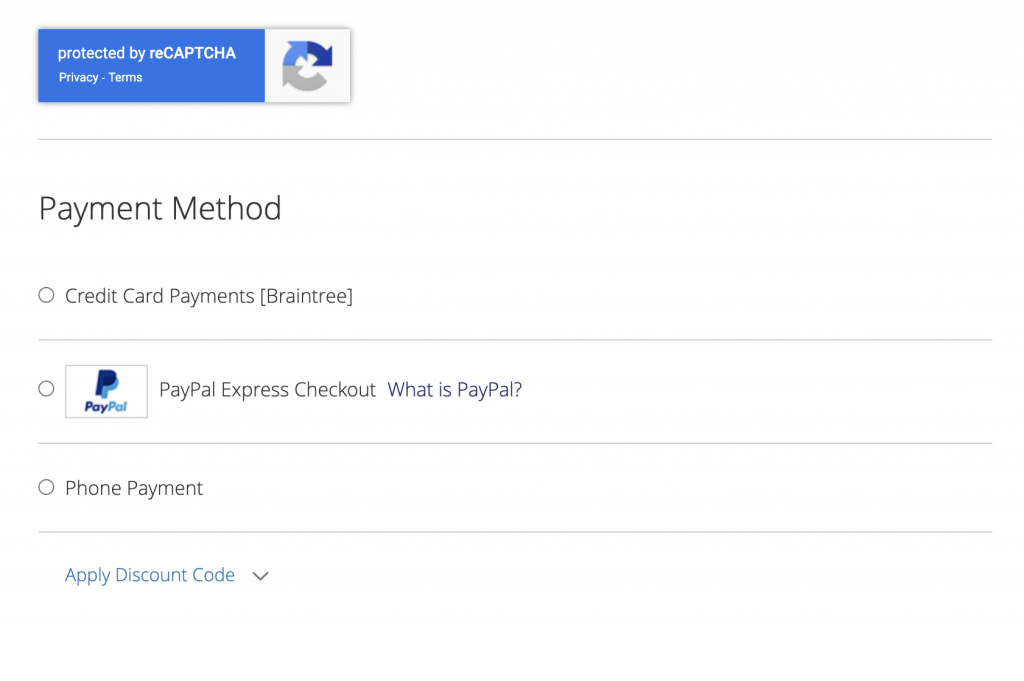
There is one drawbacks to that solution:
reCAPTCHA will be on the payment page only. Express payment shortcuts like Amazon Pay, Apple Pay, Google Pay and others might not work.
Always test all available payment methods in all places before going live.
2. Cloudflare Challenge
Cloudflare is a content delivery network service that offers firewall protection. It can help protect Magento 2 and Adobe Commerce sites against carding.
You need to add a WAF (web application firewall) custom rule. That rule will display a ‘Are you Human’ challenge to users based on various conditions.
Go to your cloudflare account Dashboard > Security > WAF:
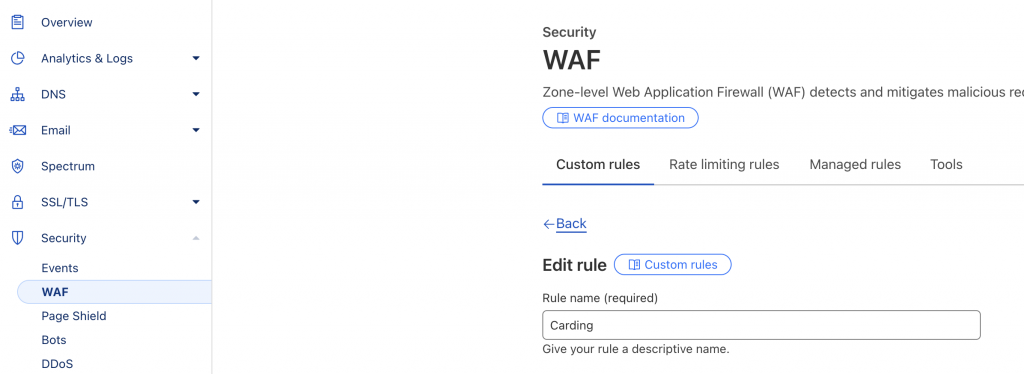
And click on create rule:
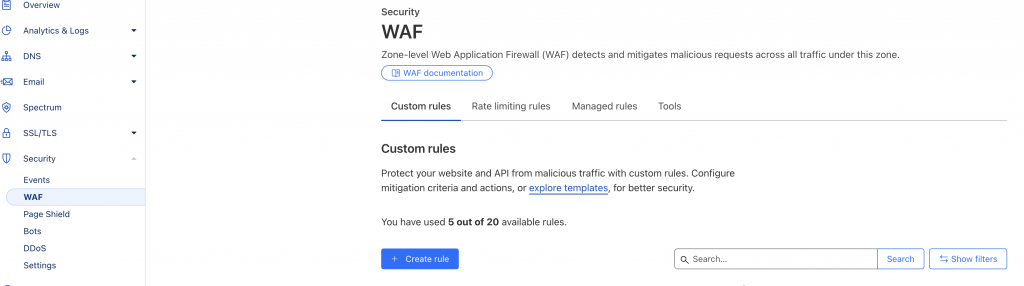
Below I’ll show a sample rule that might stop carding attacks on Magento sites:
When incoming requests match….
(http.request.uri eq "/checkout/") or (http.request.uri.path contains "/rest/" and http.request.uri.path contains "/payment-information" and http.request.method eq "POST" and not http.request.uri.path contains "Amazon" and not http.request.uri.path contains "amazon") or (http.request.uri.path contains "/graphql" and http.request.method eq "POST") or (http.request.uri.path contains "/catalogsearch/")
Then add a JS Challenge:
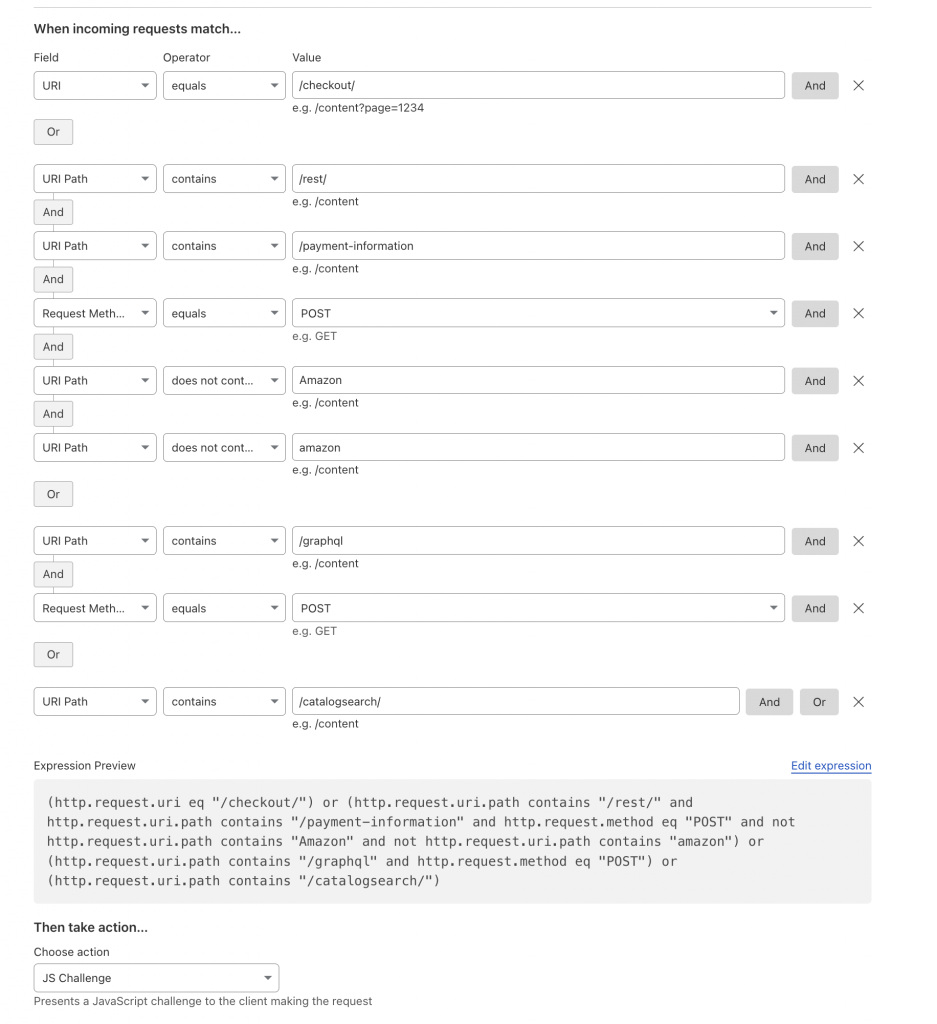
Now if you try and go to the checkout area you will see:
Once you pass the challenge you could proceed with the checkout process.
3. Rate Limiting
This is the feature of Magento 2 (Adobe Commerce) 2.4.7+ only.
Criminals can brute forcing missing information for credit cards.
Rate limiting prevents attackers from placing many orders in a short period of time.
You can set up limits at Stores > Configuration > Sales:
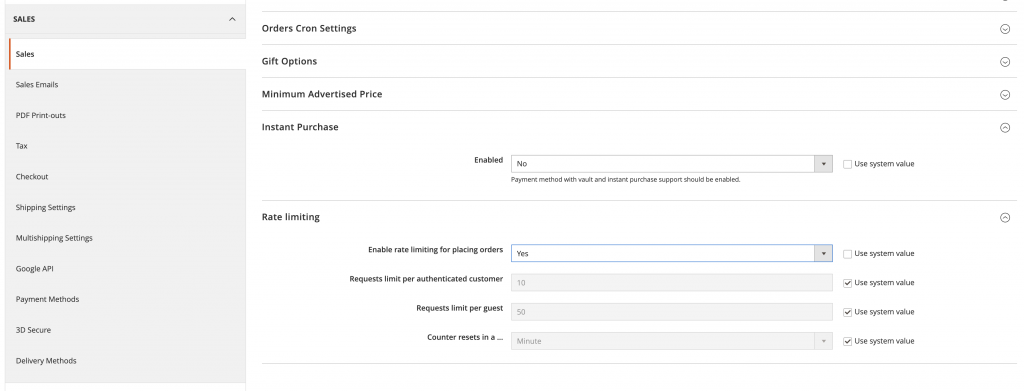
You need to establish a backpressure connection as well.
Logger keeps track of user IDs and IPs and access times to spot carding attempts.
Here is a command line to configure Redis database number 10 as a logger:
php bin/magento setup:config:set –backpressure-logger=redis –backpressure-logger-redis-server=127.0.0.1 –backpressure-logger-redis-port=6381 –backpressure-logger-redis-db=10
If a customer tries to place more than 10 orders in minute he/she will receive an error message:
Too Many Requests
4. Honeypot on the Checkout Page
There is a honeypot technique to fight spam and bot form submissions.
It works by adding an invisible form field. Bots will fill it but a real user will skip it because it’s not visible.
Server checks and flags those requests where the honeypot field isn’t empty.
We can use the same trick on the Magento Checkout Page.
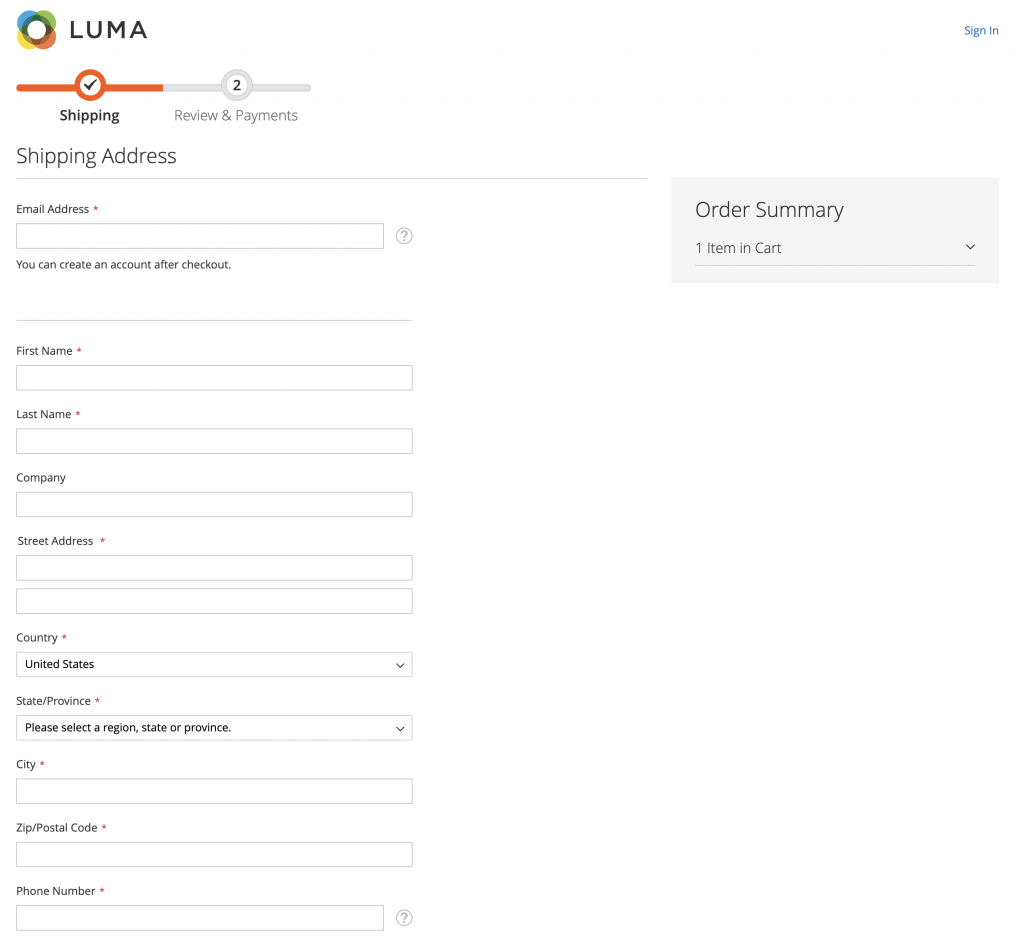
You can add an extra hidden input field to the Shipping Address section.
There are several plugins available if you are looking for a prebuilt solution.
5. Session Validation
Magento 2 offers various session validation options to filter out bogus requests.
If you go to Stores > Configuration > General > Web you will see 4 settings:

Let’s go over every one of them:
- REMOTE_ADDR: set to Yes to make sure session requests have the same IP.
- HTTP_VIA: it makes sure the proxy address stays the same for all session requests.
- HTTP_X_FORWARDED_FOR: it verifies the original IP address coming through proxy or load balancer.
- HTTP_USER_AGENT: it checks browser user agent and verifies it within one session. If a request comes with the same session ID and a different user agent, Magento throws an exception.
There is one drawback to setting REMOTE_ADDR and HTTP_VIA to Yes. A user will lose session (and cart contents) when switching from WiFi to cellular network. It could affect conversion rate in some cases.
6. Fail2Ban
Fail2ban is server software that bans incoming traffic based on various filters.
It comes preinstalled for the majority of Linux distributions.
Here is an example of how to protect /V1/guest-carts/:cartId/payment-information. Magento 2 checkout uses this url to process payment and place an order. Hackers exploit it in 99% of all carding attacks.
Let’s create a new filter /etc/fail2ban/filter.d/magento-carding.conf:
failregex = ^<HOST>.*POST.*\/rest\/[^\/]+\/V1\/guest-carts\/[^\/]+\/payment-information.*$ datepattern = %%d/%%b/%%Y:%%H:%%M:%%S
And a corresponding jail file /etc/fail2ban/jail.d/magento-carding.conf that instructs fail2ban what to do with carding abusers:
# every 1 second filter = magento-carding enabled = true logpath = /var/log/nginx/access.log findtime = 2s maxretry = 2 bantime = 30d # every 2 seconds filter = magento-carding enabled = true logpath = /var/log/nginx/access.log findtime = 4s maxretry = 2 bantime = 30d
It flags payment-information requests that come fast enough for a real user to submit.
Restart fail2ban and it should block carding attack IP addresses.
7. IP Geolocation Check
Regular real-time monitoring of your eCommerce traffic is important.
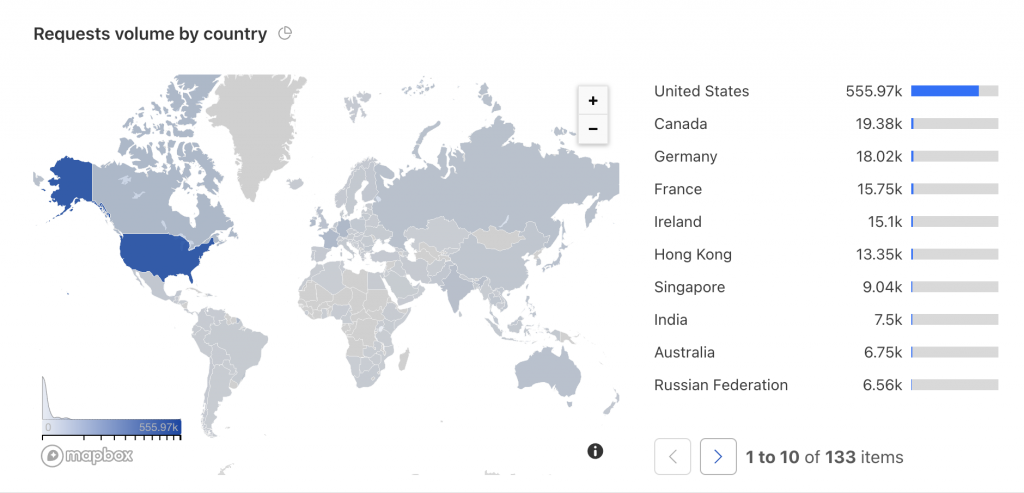
Many times a carding attack comes from a particular country (or countries). By analyzing your traffic you can spot patterns and fight back.
If you only sell within one country there is no need to be open to the whole world. You could block traffic from unwanted countries by using Cloudlfare.
There are also geolocation Magento plugins available for download on Adobe Marketplace.
Summary
Carding attacks could cost your online shop reputation and money.
There are effective ways to stop and block them forever:
- Put google reCAPTCHA on the checkout page
- Use Cloudflare JavaScript challenge
- Try fail2ban server software
- Place a honeypot to stop carding bots
- Take advantage of rate limiting if you run the latest Magento 2.4.7+
- Enable session validation functionality
- Blacklist certain countries from accessing your Magento
Do you have a question or a suggestion? Don’t hesitate to leave your feedback in the comment section below.
Do you need help with your Adobe Commerce shop? Contact me today for a free quote!
Find this article useful? Share it on LinkedIn with your professional network, spread the knowledge!
If you find this post interesting do not hesitate to sign up for our newsletter and join the 1007 people who receive Magento news, tips and tricks regularly.
Thank You!



The blog post on Magento 2 carding attacks offers an insightful look into the growing concern for e-commerce stores. The author effectively explains how carding attacks can target Magento 2 sites and the potential damage they can cause. I particularly appreciate the detailed explanation of how these attacks work and the preventive measures that can be taken, such as implementing CAPTCHA and limiting login attempts. It's crucial for Magento store owners to be aware of these threats and take steps to enhance security. The suggestions for monitoring suspicious activities and configuring security extensions are practical and valuable. This blog serves as an excellent reminder of the importance of protecting customer data and securing payment gateways. Thanks for sharing such useful information!